
Kisi Access Control
Cloud-based access control platform with mobile credentials, SSO integration, and API-first architecture
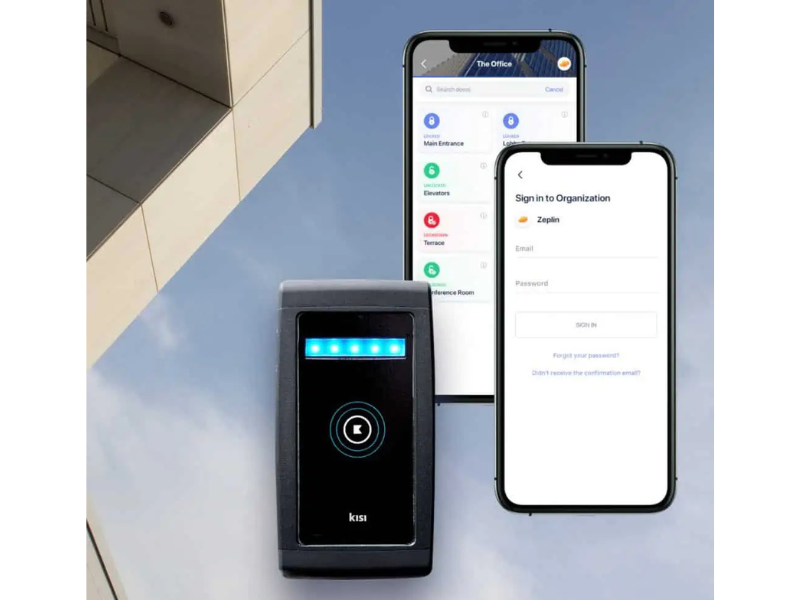
Product Overview
Kisi Access Control is a cloud-based physical security platform that replaces traditional keycards with smartphone, PIN, and biometric access for modern workplaces. It integrates with enterprise identity providers (like Okta) for real-time user provisioning and centralized management, enabling IT teams to control physical access using the same identity systems that manage digital access. The system supports both retrofitting existing Wiegand and OSDP readers and deploying new Kisi hardware including door controllers, readers (Kisi Reader Pro with 0.3-second unlock times), and intercoms across multiple locations managed from a single web dashboard or mobile app.
The platform provides granular access control configurable by endpoint, user group, or security level with customizable schedules and policies. Enterprise security features include encrypted credentials to prevent duplication, instant remote access revocation, intrusion detection capabilities, capacity management for occupancy limits, and detailed access logs for compliance and incident investigation. Mobile access supports Apple Wallet for employee badges, touchless entry, and temporary guest credentials shared via email or SMS. The system integrates with video surveillance for unified monitoring of door events and offers extensive integration capabilities through a REST API and mobile SDKs for iOS and Android.
Trusted by organizations including KAYAK, Booking.com, and numerous coworking spaces and enterprises, Kisi scales from single offices to global deployments across hundreds of locations without on-premise servers to maintain. The cloud-native architecture enables remote management from anywhere, automatic software updates, high availability, and enterprise-grade security certifications with compliance support for regulated industries. Organizations benefit from seamless migration from legacy systems, professional support, and continuous platform enhancements.
Product Details
Security Domain
Primary security domain
Key Capabilities
Specific security problems this product solves
Key Features
Core capabilities and differentiators
Integrations
Compatible tools and platforms
Deployment Options
Where and how this solution can be deployed
Pricing Model
How this solution is priced
